Managing Participant Enrollment
The Big Picture.
Q-Assessor’s ability to deploy web-based Q Methodology studies is only one half of the process. The other is contacting and communicating with the participants that you want for your studies. Q-Assessor has powerful tools that make it easy to enroll participants into your study, invite them to participate, and remind and thank them for their participation.
Anonymous vs. Enrolled Studies
Q-Assessor supports two enrollment strategies when you’re setting up a Study:
- Anonymous studies — where anyone can perform the Study
- Enrolled studies — where only participants who are specifically registered for the Study within Q-Assessor can perform the Study
In the second row of the summary table of a Study’s main page, the General Configurations panel summarizes how the Study is set to handle subject participation. In this case, the Study is configured to accept anonymous responses — meaning that anyone who goes to the Study’s URL can perform the Study. Q-Assessor provides you with the URL that you can post on your own web site, send to people, or otherwise advertise however you like. |
However, setting a Study to accept anonymous responses fails to leverage Q-Assessor’s powerful capabilities for handling recruitment to your Study. If you have a list of email addresses of a target population you want to reach, then setting the Study to use enrolled subjects is definitely the way to go.
Configuring which Study participation strategy to use is done via the “Edit study configurations” link in the “General Configurations” panel. This takes you to a form where a number of parameters are set. Specfically relevant here is the “Allow Anonymous Responses” setting. Setting this to “No” engages all the subject management tools within Q-Assessor. |
Releasing a Study
Participants — anonymous or enrolled — can only perform a Study when it’s been released for completion. Two controls in Q-Assessor handle this:
- The “Study Is Released For Responses” setting in the Study configuration form (see above) directly turns a Study “on”
- The Study beginning and ending dates affect a Study’s availability this way: each night, Q-Assessor looks through all its studies and looks for those whose “end date” has just passed — and turns those “off”
A user working on her own Study (or users within a Group working on a Group Study) can always access their own Studies regardless of these settings. It’s also always good practice to open a Study to responses but have a few collaborators try it out first before notifying your actual study population to do the study.
These settings allow you to develop and test a Study yourself to make sure it’s ready to go when you finally do engage your subjects.
Enrolling Participants
This section deals with the most common case when using Q-Assessor — identified, enrolled Subjects. Typically you would have a number of email addresses for people who you want to complete your Study.
Q-Assessor gives you two ways to enroll these subjects:
- A simple form lets you “register” them one at a time
- A “bulk upload” form lets you paste in a list of people and register them all at once
These forms are reached from the “Manage Enrollment” link in the “Enrollment” panel of the Study’s main page summary.
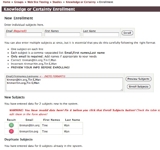
This screen-shot shows these two forms. In particular, note the “bulk enroll” form, which clearly specifies the correct format for each participant’s data. Note also the Preview Subjects button and its results — either a “green light” everything-is-OK result or a “red light” there-are-errors warning. Always preview your subject data before bulk uploading! |
As you enroll subjects, they will show up in the “Current Enrollment” table that is located just below the “New Enrollment” forms. This table contains lots of important information — the Subjects’ unique subject codes (created and maintained for you by Q-Assessor), their email addresses, their status in the study, and timestamps of important events — when they were invited, when they were last reminded, and when they completed the study. You can remove them from the Study via the “Remove” link, and you can edit their email address and names via the link associated with their subject codes. |
Inviting and Reminding Participants
As you enroll participants, they are added to Q-Assessor’s database — but they have not yet been notified about your study. This involves a specific step — inviting your subjects — so that you can enroll a number of subjects and then invite them all at once.
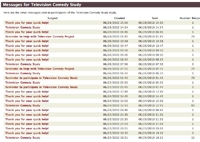
The section below the “Current Enrollment” table always tells you the current status of invitations and reminders. In this screen-shot, one newly enrolled subject needs to be invited, while 69 subjects are due for reminders. |
Handling Emails to Participants
Q-Assessor provides a powerful system to let you communicate with your participants at the point you invite, remind, and thank them. Here’s how it works:
- You compose the basic wording of all three sorts of emails when you configure the Study itself.
- Q-Assessor will automatically insert into the invitation and reminder emails special customized links — particular to each individual subject — that the subject clicks to get back to the Q-Assessor web site to complete your Study. Q-Assessor places these links automatically at the end of your emails, and it uses the language that you’ve configured your study to use.
- Q-Assessor generates two kinds of links — the link that subjects click in order to participate, and the link that they click to refuse. (When subjects refuse, their enrollment is updated accordingly and they are given a simple “thank you anyway” page.)
You can see the results of this in the “Subject Emails” section of the Study’s main summary table. This screen-shot shows an example. Everything prior to the “Here is the link to participate” line is what the owner of the Study wrote; everything after was inserted by Q-Assessor. You can edit your email boilerplate text by clicking the “Edit emails” link below the emails themselves. |
When you manually send out emails — always the case with invitations, and optionally the case with reminders — you reach this form. Your basic boilerplate is inserted for you, where you can further edit it as you like before you actually send the emails. |
Of course, when Q-Assessor sends out automated reminders for you in the middle of the night, it simply uses your boilerplate exactly as it is.
All emails Q-Assessor sends out for a Study are archived for review. The “Email Archive” section at the bottom of a Study’s main Enrollment page tells you how many emails have been sent. Clicking this link brings up a list of the emails along with information about how many recipients got each one and when they were sent. Clicking a specific email then shows you the actual text sent as well as the specific recipients. |
Confidentiality Issues
If your study requires Institutional Review Board (IRB) approval, here are a few points that will be useful in your discussions with them:
- Participant consent is intrinsically obtained thus: In the study introduction should go all information that a participant needs to know in order to decide whether or not to participate. Each participant must explicitly click a “Start the study” button before they can start — which completely signifies their choice to participate. This mechanism has satisfied every IRB that has reviewed it.
- Participant “confidentiality” can be irretrievably insured by configuring a study to accept anonymous participants. The system then will have no information about any participant other than whatever information the investigator asks them to provide in the post-sort interview questions, along with an IP address — which is in most cases a non-routable address randomly given the participant by their ISP when they access the Internet.
- Access to any investigator’s account and thus study data is limited to that investigator, optionally others in a group if we set such up for the investigator, and the Q-Assessor site administrator. The latter access is necessary in order to provide support as well as to monitor for inappropriate use by any user. The server technologies use industry-standard database and middle-ware tools with strict access controls. However, the server hard drive is not “encrypted,” which in any case would not be useful apart from some sort of physical attack on the server, which is improbable given that the hosting service is “out there” in the “cloud.”
Created: August 04, 2010 17:17
Last updated: June 03, 2015 00:45






Comments
No comments yet.
To comment, you must log in first.